@dsrv/kms
Sign Transaction General
We'd like to look at the conceptual information contained in transaction signatures before moving on to the tutorial on sending transactions by chain using the @dsrv/kms package.
1. About Encryption
Encryption is a method used to hide sensitive information from prying eyes and prevent unauthorized access, as well as to validate the validity of published papers. In blockchain, asymmetric key cryptography is a term that describes the usage of various keys for encryption and decoding. The two distinct keys are referred to as private keys and public keys, which is also known as public-key encryption. Then, how do these encryption techniques function to verify the legitimacy of documents? Let's examine the following example.
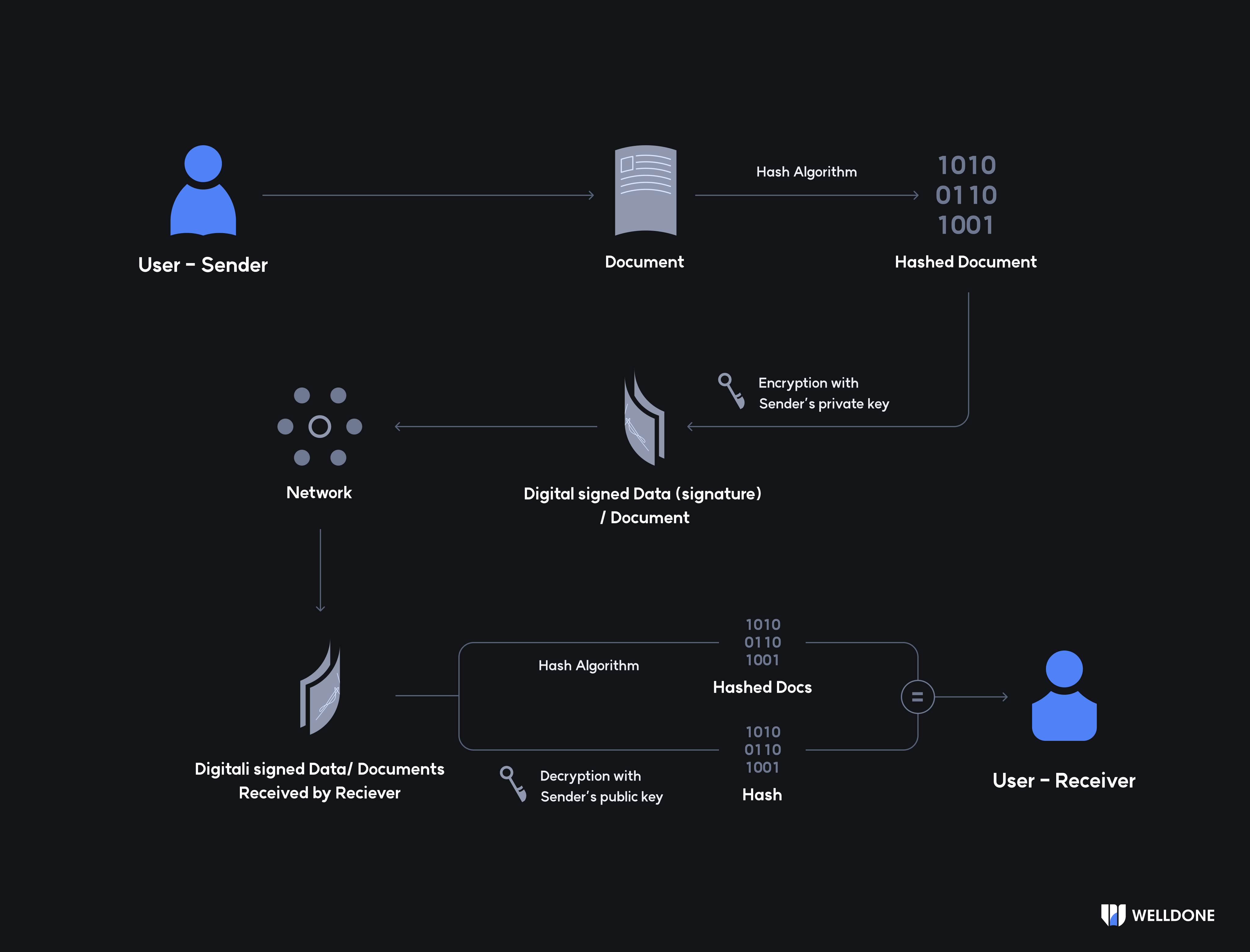
- Using an asymmetric technique, Alice creates a pair of key pairs. - Alice can validate her identity using a public key.
- Alice hashes the plaintext to send and reduces it to a predetermined length.
- There are items in the plaintext that identify the author.
- Public keys are contained in the item.
- Utilize Alice's private key to sign the sentence's hash.
- Alice can then obtain the sentence's signature.
- Alice delivers a signed message(plaintext and sentence's signature) to Bob.
- Using the signature and the public key in plaintext, Bob may decrypt the plaintext again and retrieve the hash value.
- At this stage, Bob can be certain that Alice created the phrase if he or she has the same hash value as the hash value obtained through decryption.
This public key strategy's primary feature is that messages signed exclusively using Alice's private key can only be unlocked using Alice's public key. Since Alice's public key may be used to decrypt messages, it is possible to tell whether or not someone else signed and sent the message because the original content will not display correctly.
2. Encryption used for transaction transmission
So how does blockchain use the asymmetric encryption technology that establishes authenticity stated above? When sending transactions on the blockchain, encryption is primarily used to verify the legitimacy of the transaction. If a user requests that money be transferred from Alice's account to Bob's account via a blockchain transaction, the blockchain node must be able to confirm that the user is the rightful owner of Alice's account. Let's examine the examples below to help you grasp this.
- A user encrypts a transaction statement by signing it with a private key and transferring money from their account to Bob's account.
- By signing the transaction, you can collect signatures.
- Transmits signed transactions to nodes in the third party.
- The node will now verify the legitimacy of the signed transaction.
- To decode the transaction, the node uses Alice's public key since it believes the author to be a transaction signed by Alice.
- You can tell if a transaction is genuine by comparing the transaction text that was decrypted using Alice's public key to the original transaction.
If you look at the sdk of the chains, each transaction has its own serialize and deserialize routines. All blockchains contain serialize standards that turn transactions into byteArray. Before signing, the ByteArray that results from serializing the transaction is just plain text. The private and public keys in your wallet serve as the signature keys and the address of the blockchain that you control.
Tutorial
# using npm
npm install @dsrv/kms
# using yarn
yarn add @dsrv/kms
Each chain has its own individual procedure for using @dsrv/kms to transmit transactions, however most chains adhere to a standard procedure.
- Using SDK, generate raw transactions for each chain.
- Obtain a signature by using the
signTxmethod of@dsrv/kms. - Combine the raw transaction produced earlier with the signature produced by
@dsrv/kmsto create a signed transaction.
- Combine the raw transaction produced earlier with the signature produced by
- The signed transaction is sent across the SDK by chain.
Sending transactions by chain is explained in great detail in the Chain by section.
For individuals having a foundational understanding of HTML, CSS, and JavaScript, this tutorial is advised.
📄️ Aptos
Sending Transactions using @dsrv/kms in Aptos
📄️ Celo
Sending Transactions using @dsrv/kms in Celo
📄️ Cosmos
Sending Transactions using @dsrv/kms in cosmos
📄️ Ethereum
Sending Transactions using @dsrv/kms in Ethereum
📄️ NEAR
Sending Transactions using @dsrv/kms in NEAR
📄️ Solana
Sending Transactions using @dsrv/kms in solana